This tutorial we are going to perform steps for how to restrict an AWS IAM user’s access to a single S3 bucket.
S3 becomes actual standard for publishing files in the internet. When we work with the team, we might want to restrict an access of single S3 bucket to specific users. You can do it in IAM as follows.
Create a policy for AWS bucket
Go to Services >> IAM >> Policies >> Create Policy >> JSON >>
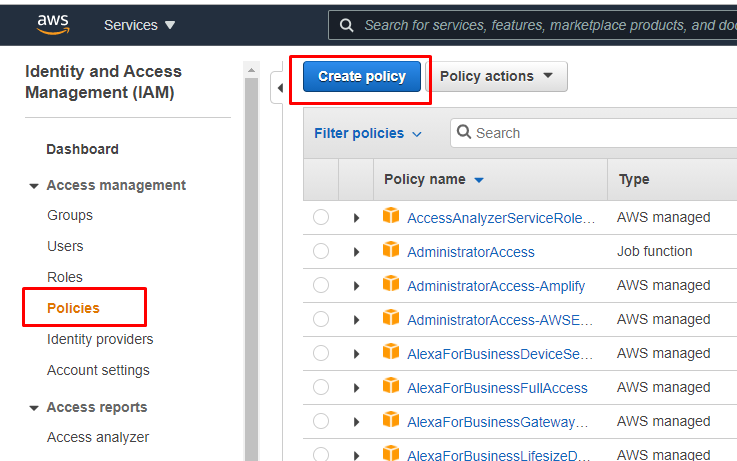
Inset below policy here.
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Allow”,
“Action”: [
“s3:GetBucketLocation”,
“s3:ListAllMyBuckets”
],
“Resource”: “arn:aws:s3:::*”
},
{
“Effect”: “Allow”,
“Action”: “s3:*”,
“Resource”: [
“arn:aws:s3:::YOUR-BUCKET-NAME”,
“arn:aws:s3:::YOUR-BUCKET-NAME/*”
]
}
]
}
PS: Please change YOUR-BUCKET-NAME with your S3 Bucket name.
Now click on ‘Review Policy’
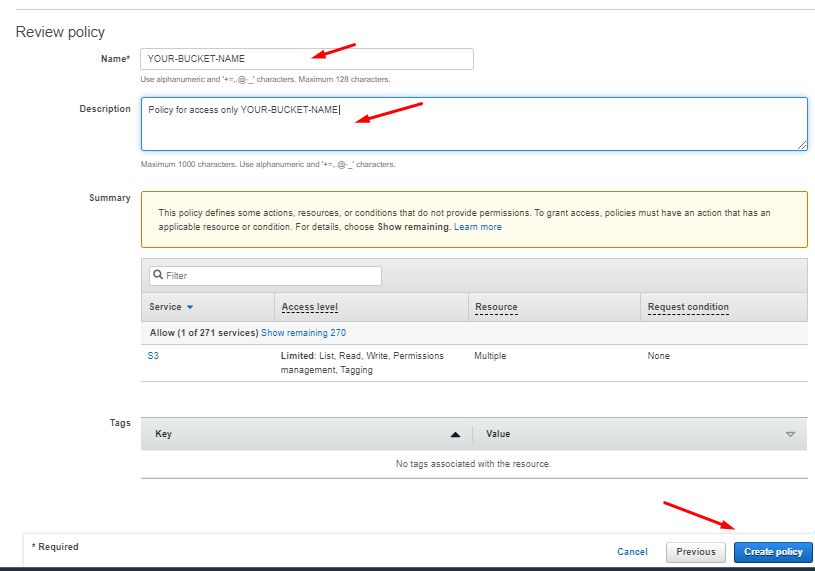
Here it asks for policy name and description. After insert detailed click on ‘Create Policy’ button.
Now AWS created a new policy for only single S3-bucket access which named you to insert in policy.
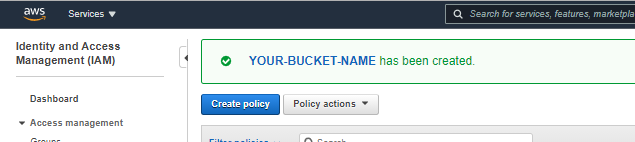
Attach Policy to User and Group
Now attach this policy which user or group, you want to access only that bucket which mentioned you in policy and restricts remain bucket access.
For Now I am creating a New user and attach policy to that user.
Go To: Users >> Add user
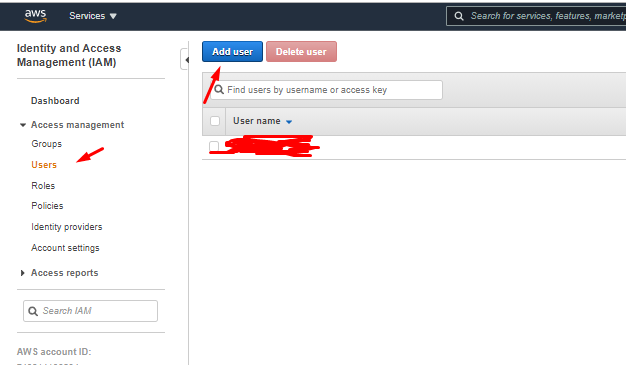
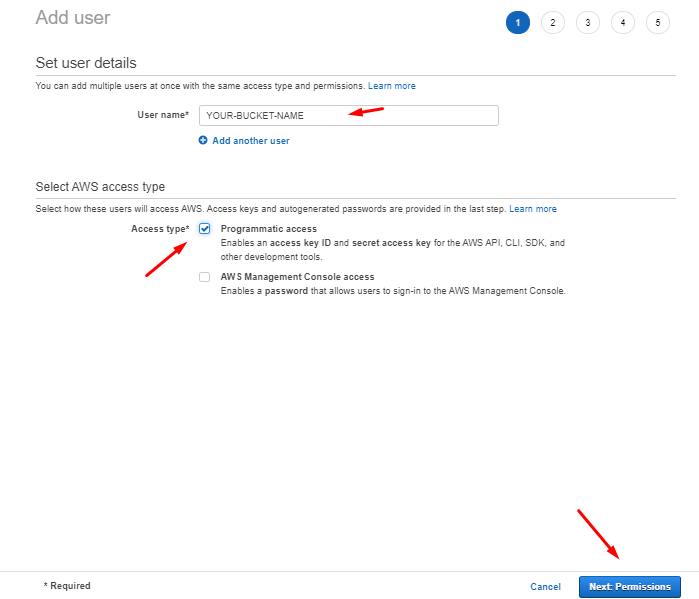
After click on add new user enter your user name, Select Access type Programmatic Access and click on Next:Permissions button .
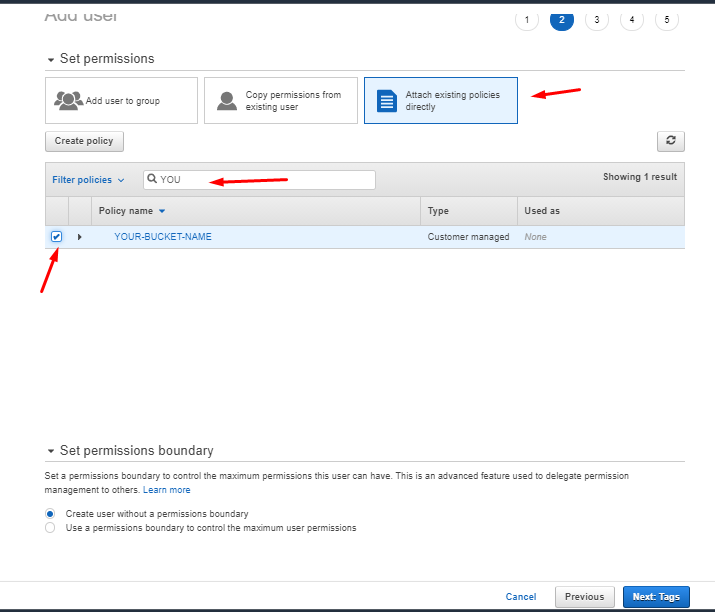
After that you will redirected to new page than select Attach existing policies directly.
In search bar enter your policy name that we have just created few mins ago, Select policy and click on Next:Tags Button.
than Next:Review Button and Create user.
NOTE: These credentials are visible and available to download as .csv file only once. So it’s better to save them in your system.
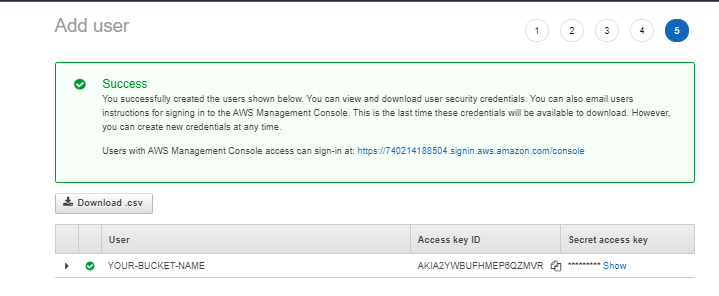
Now configure these credentials in your system to access bucket.
All! Done






